insert_linkYour Privacy: It’s Progressively Diminishing
This privacy guide is brought to you as a necessity for those who dislike the idea of being constantly watched. After all, why shouldn’t we have the right to protect our data?
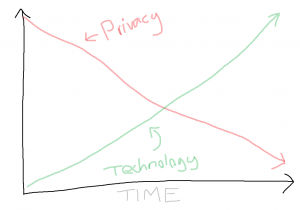
Alas, the trend over recent times shows an inevitable decline in privacy. The Internet, smart home devices, the rise of cameras, and wearable technology are all indicators of this trend.
Development of technology, besides an exciting, convenient future, results in the reduction of privacy.
Indeed, we could all forget about this privacy guide, accepting the inescapable reality yet to come. There is, in fact, an insightful article about the declining privacy trend here, if you’re interested in learning more.
Sometimes, however, we don’t need to be providing data to such an extent—why a privacy guide is useful.
To iterate, the reality is that we are slowly losing our privacy everywhere with technology. That doesn’t mean we can’t secure certain aspects of our lives, though.
If you’re the hero, hacking scammers’ computers, you’re most likely against being tracked.
The ultimate purpose of today’s privacy guide is to provide you with the resources to:
- Reclaim your online privacy
- Become more anonymous online
- Make sure your data is secure
- Stop Windows 10 from spying on you
Pay with privacy: How to Use Bitcoin: Truths You Need to Know
insert_linkThe Power of Data

insert_linkWhat Data Can Be Collected About You
It turns out that tracking your activities can generate a vast quantity of data. Furthermore, this is all information about you.
For instance, the vast majority of websites you find online utilise tracking technology. That is to say, websites have the liberty to track and record your every move.
Of course, what it is exactly that is tracked varies between websites, for an assortment of reasons as to why.
To exemplify, a common use of tracking data is for analytics; this allows the website to understand the behaviour in addition to other statistics of their users. It could even go as far as producing demographical data such as your gender and age.
Despite collecting huge butter-tub-loads of the users’ data, in most cases, there’s nothing to personally identify them. With that said, a lot can be done when you have access to many people’s IP addresses.
insert_linkHow People Handle Your Data
But what can this data be used for?
Naturally, this sort of data can be used in a plethora of diverse ways, as well.
In an ethical scenario, analytics are not used to compromise people’s privacy, but to serve them better. This could consist of, to enumerate, optimising website content, marketing strategies and products.
Obviously, you would want content that is best suited for you, since that’s when you get the most value.
Conversely, this information can be used by adverts on the website to trace your steps as you surf the online. This means advertisers can know exactly where you’ve been and what you’ve been clicking on.
Information like this isn’t just available to advertisers, to clarify, but it’s where it is mostly used: to display personalised advertisements based on your interests.
Data can additionally be sold to advertisers and other 3rd parties as a way to make some profit.
As a matter of fact, tracking technology can build up a frighteningly detailed profile of your online presence.
insert_linkNot Just Web-Browsing

Moreover, if that wasn’t disturbing enough, websites aren’t the only things that track your activities. Software you may use everyday could, in actuality, be collecting a vast range of data as you use it.
Have you wondered why this is a privacy guide for Windows 10, as opposed to a general privacy guide?
While Microsoft isn’t alone in this, Windows 10 is used to scrape up an unimaginable library of your usage data. Besides, it isn’t exclusively usage data that is collected—sensitive stuff like account information is gladly Zucked.
Furthermore, this data can be personally identifiable if you don’t know how to wear a virtual mask. Relying on this privacy guide, though, you will be able to hide your traces and opt-out of the tracker party.
insert_linkA. Online Privacy Guide (Any Operating System)
The Internet, rather evidently, is potentially the largest outlet for your data. And there’s no surprise there.
The first part of our privacy guide capitalises on sealing the data gaps as you surf the online world. However, before we let ourselves get too far ahead of ourselves, let’s conduct a brief sanity-check.
Your online behaviour makes a massive difference when evaluating the meaning of your online privacy.
To get to the point, this privacy guide won’t help you if you have the tendency to give away your data for free. This applies to your sensitive information (such as your banking details) more than anything else.
insert_linkAn Online Guide to Privacy: Quick Tips
insert_linkWatch Your Website: It May Want to Get You
Navigate only to the websites you trust, without an exception. Likewise, don’t visit any website that has the potential to be malicious in any way.
Don’t worry if you can’t be sure regarding what’s dodgy and what’s not just yet; I have written a useful article that can help you identify scams, including those questionable websites.
Don’t Give Away Your Information: How to Spot a Scam in 3 Simple Words
Equally, don’t fret if you think you have visited scam-like sites that might have infected your computer. It is unfortunately incredibly difficult to avoid unwanted websites; thus, you’ll benefit from advice later in this privacy guide.
Occasionally, you may need to access a potentially malicious website for whatever reason, or you aren’t sure about a certain website.
I dictate that, in this case, it would be wise to use a virtual machine. Although, as this may not be a convenient option for everyone, at least use the tools I’ll show you later.
insert_linkWatch Your Information: It May Come Back to Haunt You

As if you haven’t heard this tip enough times already in the past 3.14159 years.
The aforementioned reality that privacy is becoming a thing of the past is something we must currently accept. Do not try to fight it—or, alternatively, avoid it—therefore.
Even though this might sound slightly seat-shuffling to you, embracing this reality is easier than you think; it entirely revolves around your decisions as to what information you make available online.
For an extreme illustration of this: imagine releasing your home address to, for example, your Twitter followers. You can’t expect it only to be seen by the people you trust, because it’s now entirely public.
Any information, for that matter, which you provide online services with, should be considered entirely public. This is in spite of the idea that that information would be handled responsibly, respecting your privacy.
Admittedly, companies can respect your privacy, hence keeping your information private and secure. This does not mean, however, that you should treat such data as private—think of it as public.
Except that, in the case of an email address, for instance, you may not always receive spam from the public. Nevertheless, less reputable, less trustworthy sites could mistreat and abuse your email, phone number, and the like.
Therefore, always be sceptical and cautious over the information you give out.
Likewise, be careful when voicing your opinion online—as it might just be your future downfall. Opinions are liable to change, after all.
insert_linkUse the Best Search Engine Available
Opening up the real deal of this privacy guide: don’t use Google, regardless of how popular or respected it is. Google is so infuriatingly common and well-known as a search engine that it has a verb named after itself.
To illustrate, here’s the real definition at Oxford Dictionaries:
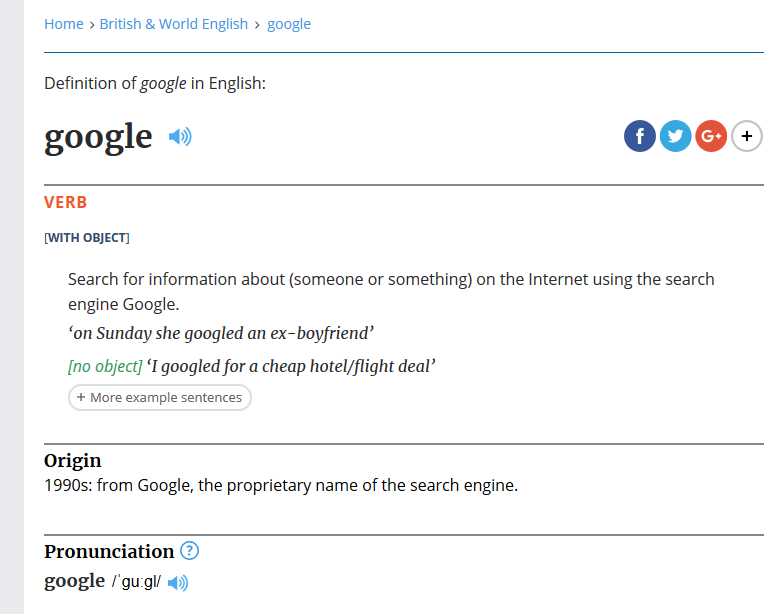
Hey, wait a few glorious seconds while I GOOGLE that for you…
Tell me—is that, or, by contrast, is that not, completely, utterly, aggravatingly shocking?
Not to mention, it comes to its knees with regards to privacy—something merely a few knows anything about.
insert_linkThe Problem
Google tracks your soul out of you. In addition, this data is used, not only to be sold to advertisers, but to “personalise” your search results.
Perhaps this is why the population’s majority love, swear by, and fight for Google’s search results; perhaps it is because of the relevance of said results…
It is nonetheless possible to experience the thrills of an exceedingly potent search engine without the excluded privacy.
In preparation of you having second thoughts about this plan, I urge you to trust me. Do you, more importantly, trust Google with every individual search you make?
Upon thinking about it, you will find that your search queries will reveal an enormous amount about you. Take this privacy guide, then—in your pocket—like you would with your suspicious map of the bank.
insert_linkThe Solution
The secret to concealing your online searches is to use an alternative search engine, namely DuckDuckGo and StartPage. For a complete article about these—as well as cool search tips—click me.
Be like the hackers: What is The Best Way to Search the Internet?
To be concise, DuckDuckGo is an exceptionally powerful, private search engine based on Bing. StartPage, on the contrary, is based on Google’s search engine, yet offers privacy and anonymity.
“How could this possibly be, Big Davis, if they use the search engines that track you, yo?”

Firstly, my name is not “Big Davis”. Secondly, these search engines are private since they get the results, not you.
As a result, there is no way in which Google—or Bing—could track what you are searching; for you see, all they know is that something is being searched.
“Yes—okay—that seems pretty toasty, but, I must say, man, yo, what’s poppin’ with dem search results?”
Well, as far as the results go, they truly aren’t that bad. Personally, I’ve been using DuckDuckGo and I have never had a problem in that respect.
With that said, if you are fussy with results, the latter option—StartPage—is for you. This is because it will straightforwardly feed you Google’s results, albeit those which haven’t been tampered with.
insert_linkSecure Your Privacy with Browser Extensions
Are you not totally convinced with the idea of swarms of trackers wherever you go online? That’s highly convenient given that you can easily block trackers online, securing your privacy.
insert_link1. Ghostery
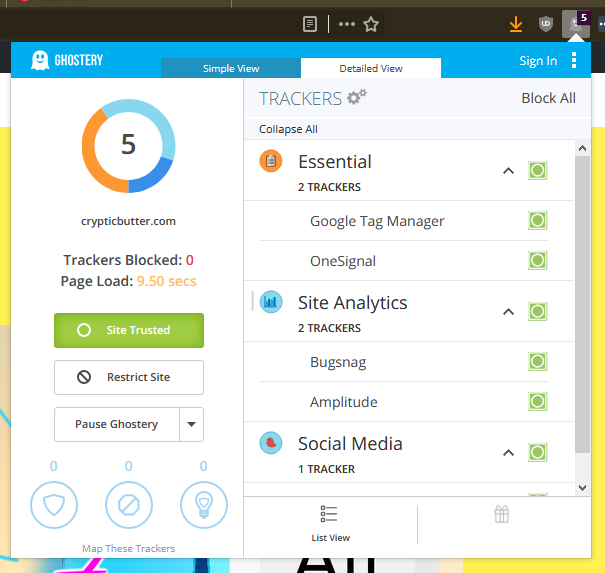
Firstly, we will be installing Ghostery on our browser of preference (preferably that preference is Firefox). This extension blocks trackers as you surf the web, and can be customised to block specific trackers and categories.
Moreover, blocking one too many trackers could break a site or remove certain functionalities. Therefore, this extension allows you to trust that troublesome—yet essential—tracker for the website.
There is, alternatively, a “trust site” button for letting all the trackers on the website roam freely. Let’s move on, having got that critical information pushed out of the way.
insert_link2. uBlock Origin
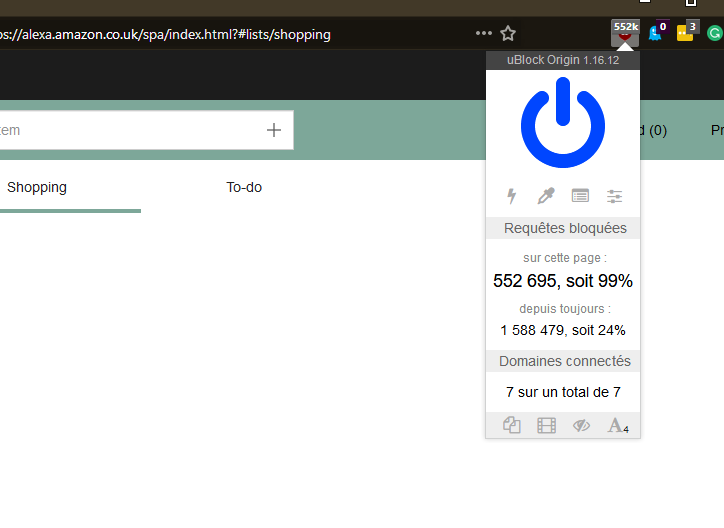
Secondly, with added protection (and privacy) against those shady advertisements, uBlock Origin is simply the best ad-blocker around. It works flawlessly.
Important note: there is no official website for uBlock Origin; get it with assistance from that page on GitHub.
Using an advertisement-blocker like this, if truth be told, is something actively discouraged by a large number of websites. It is for the reason that websites maintain a revenue source through these advertisements.
If this is something that concerns you, I have an intriguing article all about the matter. Keep in mind, though, that uBlock is actually a “wide-spectrum blocker”, and blocks trackers too.
See the argument: 5 Eye-Opening Reasons Why I Happily Block Ads
Again, as with Ghostery, uBlock Origin has the ability to whitelist a website—or even a page. Another advantage that won’t go in through one eye and subsequently out the other is that it is lightweight.
It won’t slow your browser down such that you might it’s faster to be accepting all those slow advertisements.
insert_link3. Bitdefender TrafficLight
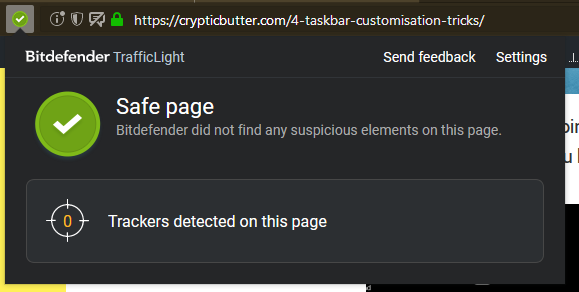
Thirdly, you should get yourself something to help avoid those dodgy websites. Bitdefender TrafficLight is, in my opinion, the best of the bunch.
It’s honestly as effortless as installing the plugin, which subsequently causes the icon to appear in the toolbar. Most likely, it’s now looking like a nice, great, big green tick, thus indicating that the current page is safe.
If it so happens that you stumble across a best-avoided type of website, Bitdefender will be sure to tell you. It has a respectable database of phishing websites, albeit don’t expect it to catch everything.
Despite having served me well, I have found that some websites are not on the list. Consequently, you will have to send feedback regarding this on identifying a new phishing attempt.
insert_link4. OpenDNS
Providing an additional layer of filtration, check out OpenDNS to prevent stumbling upon websites you don’t want to land on. While the Family Shield option is set & forget, the Home plan offers more control over what is blocked. The latter also supports monitoring tools.
The noteworthy element of OpenDNS is indisputably the ability to block phishing attempts as well as malicious websites. So, when you click on that link, 100% persuaded that it is clean as dishwashers, OpenDNS will make you think again.
insert_linkBecome Anonymous with These Simple Tools
You’ve done a spectacular job thus far, but ground remains to be covered. Next, we’ll take a peek at some more tools you need to have installed immediately.
insert_link1. A Truly Private, Secure and Fast VPN
Nothing beats a solid VPN (Virtual Private Network). If you were to ask me what defines a good VPN service, it would go along the lines of:
One that securely encrypts all of your network traffic meanwhile providing remarkable Internet speeds. That is, all without monitoring your traffic or keeping logs—i.e. maintaining a stellar privacy-policy.
This would not be a privacy guide worth listening to (with your eyes) if there was no good VPN. Concealing your IP address, hence your identity, good VPNs keep you anonymous and out of the eyes of your ISP.
Did you know—your ISP (Internet Service Provider) could be monitoring your traffic as you use the Internet? Thought-provoking, indeed.
Comprehensive Comparison: Private Internet Access vs NordVPN? The Best Deal (Aug 2018)
So, get secure besides giving yourself some space. For example, I suggest the best VPNs are IPVanish and NordVPN—both with startling speed, privacy and security. Here’s a quick comparison of their differences:
| NordVPN | IPVanish |
| 6 Simultaneous connections | 10 Simultaneous connections |
| $6.99 for 1 year* | $6.49 for one year* |
| 30-day money back | 7-day money back |
| “Double VPN” for double the encryption | Perhaps has the slight edge for speed |
*Prices representative of those advertised at the time of writing.
Trust me, you can’t get away with a free VPN, as most of the time, they monitor you and keep logs. Also, they invariably have strict monthly data caps, so don’t expect to be using them on the regular.
Have you picked a VPN yet? Great, because we’re moving on.
insert_link2. The Tor Browser for Risky Biscuits
Tor, similarly to a VPN, goes to certain measures in order to mask your IP address. That’s right—we’re not stopping at VPNs in this privacy guide, rather, we’re going the full stretch.
Of course, you can always read up about it yourself for the purpose of gaining a clearer picture. For the purpose of a comprehensive privacy guide: I will nonetheless outline a few points as to what it is and why you might need it.
If you want to be as anonymous as possible, Tor, by masking your location and using encryption, is for you. When using the Tor browser, all of your traffic is randomly routed through Tor nodes.
The website you visit, therefore, cannot know it’s you from purely the IP address they see.
Here are a few ideas which highlight the benefits of using Tor:
- You can maintain your physical safety with the online privacy.
- Price discrimination (from websites tracking your activity) can be avoided.
- Your job security is all right in the event that you work for a government agency.
Plus, Tor is widely used by:
- Individuals like you and me, for that added privacy bonus.
- The nonsensical journalists who hate Elon Musk (great man, by the way).
- A branch of the US Navy
- Corporations
- Activist groups
Learn with Tor: Future of the Space Industry: Why Should You Be Excited?
Tor can additionally be used to route all of your computer’s traffic through the network. Advanced Onion Router, for example, is a Windows application that allows you to do precisely that!
As a result of this, you will be able to anonymise all the traffic that leaves your computer; including the potentially privacy-compromising of such.
insert_linkWhy Tor Doesn’t Remove the Need for a VPN
Be that as it may, I thoroughly disbelieve the concept that Tor can fully replace a VPN. Indeed, it serves a similar function, and boosts online privacy—but it has some downsides.
To begin with, try using the browser yourself, since you’ll find some of the drawbacks yourself. Firstly, I wouldn’t use it as my primary browser seeing that when you open it, you’re totally anonymous.
There is no automatic login, meaning you must sign into every service you want to use, as such. Equally, browser history becomes a thing of a past, so don’t expect to be finding that one page again.
Secondly, it’s quite slow compared to using a quality VPN like those aforementioned. This is admittedly acceptable given the privacy benefits, though.
Navigating the web for your typical daily information, however, the Tor browser could be avoided. Downloads, too, are severely compromised in terms of speed.
Thirdly, you get enhanced privacy and security by using Tor in conjunction with a VPN!
insert_linkB. Windows 10 Privacy Guide
Wow, that is already 3000 words of privacy-guide done and dusted thus far. I must say that, to all the Mac, Linux, and other users out there, you can go hop along somewhere else.
Take me for a spin: Go somewhere random!
Better than QWERTY: How to Learn Colemak Effectively: The Best Strategies
By a far stretch of the butter-tree woodland, the best way to boost your Windows 10 privacy is this tool: the easy and straightforward O&O ShutUp10 application—available for free.
Take the time to note that this application is portable, meaning you do not install it. By contrast, you download the programme as a single executable file.
With that in mind, download ShutUp10 from the provided link, then save the file somewhere you’ll remember. (If you want, you could put it—or a shortcut—onto the desktop for convenience.)
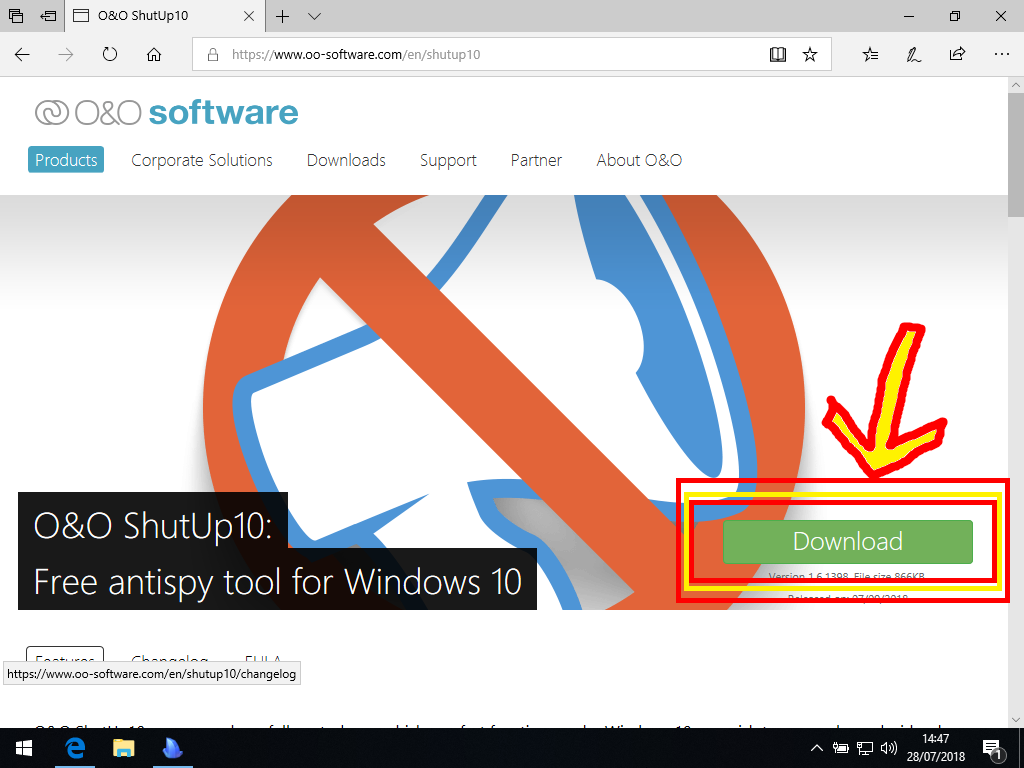
Next, find and run the programme, which results in a new window opening up.
Don’t mind me borrowing some text from this resource:
Now it’s simply the case of going through each setting and deciding whether it should be enabled or disabled. Remember that green represents privacy and security, whereas red is clearly bad.
However, to make life, easier, you can go to Actions and enable all recommended settings. These, as implied, are the safest settings to trigger. For more information about a particular setting, you can straightforwardly click on the setting’s corresponding text.
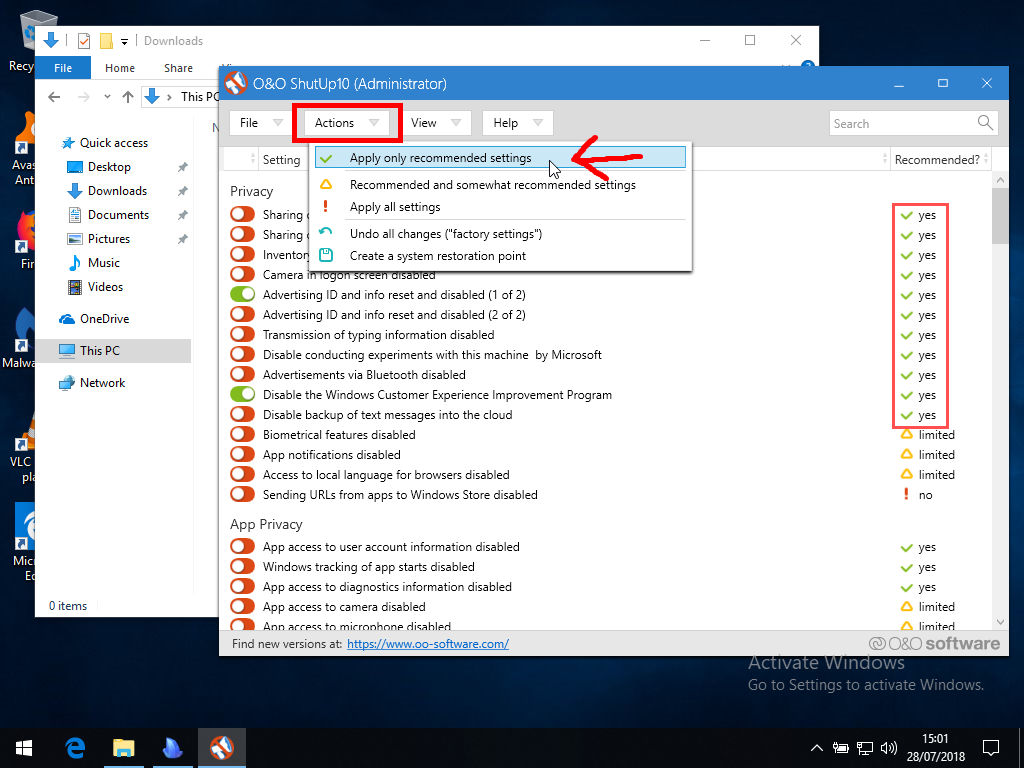
Also, the application will ask you to make a restore point, which I recommend. This is because if you do make something go wrong, you can always revert the changes in the future, essentially.
insert_linkNicely Done, But There's Still More to Come
Quite frankly, this application is your one-stop shop for most privacy-related things. Furthermore, the reason I told you to put it somewhere you’ll remember is that you’re not done with it.
Windows 10, being anti-privacy in nature, will want to enforce its data-collection techniques upon you whenever it can. As a consequence, updates—chiefly the major ones—will want to reset your privacy settings.
To combat this, you can, following an update, open the ShutUp10 application and choose to revert the settings back to how you previously had them; it remembers your settings and detects changes since last opening it.
This way, you can ensure your privacy is top-notch—doubtlessly after following this privacy guide.
If you want more information about setting up Windows 10 in the most optimal way, see this Windows 10 guide. There, I guide you through the steps towards making Windows 10 fast, secure, and private.
Do it the proper way: Ultimate Checklist for the Best Initial Windows 10 Setup 2018


